Smart Data is the Standard for Trustable Digital Assets
The Smart Data Protocol integrates a growing ecosystem of Trust Envelopes into a single solution that provides Digital Asset interoperability, ownership, security, control, privacy, and monetization with unparalleled trust.
Learn more about Security, Integrity, Ownership, and Intelligent Envelopes.

Smart Data Protocol Security Envelopes
Standardization
Standardization ensures data interoperability across different systems and organizations. Democratically created standards allow for transparency, collaboration, and community-driven improvements. Standardization eliminates the need for expensive custom integrations, enabling a more seamless multi-party data exchange. Most importantly, standards promote inclusivity, innovation, and avoid vendor lock-in.
Productization of Digital Assets
Security Envelopes are self-contained data objects that encapsulate the data itself, metadata about the data, and the logic required to process and interpret the data, promoting the productization and reuse of Data Assets. Harvard Business Review,“A Better Way to Put Your Data to Work,” maintains that when companies treat their data like a product, they can:
- Reduce the time to implement new data use cases by as much as 90%.
- Decrease their total cost of ownership (technology, development, and maintenance) by up to 30%.
Data Masking & Access Control
Security Envelopes provide data masking and obfuscation encryption techniques to protect the confidentiality of the data they contain. They include access control mechanisms to regulate data access and modification. By implementing access control mechanisms, Security Envelopes allow organizations to enforce data privacy and security policies across multi-party data collaborations. This solves the problem of unauthorized data access or modification, enhancing data governance and compliance across multi-party data transactions.
Flexibility & Innovation
Security Envelopes are flexible and extensible, allowing for the inclusion of additional features, changing data requirements, and technology advances. Security Envelopes can accommodate new data formats, business rules, or integration requirements, promoting data agility and reducing data debt.
Toda Protocol Integrity Envelopes
The Toda Protocol provides digital asset provenance and transaction integrity. It introduces Cryptographic Proof of Provenance combined with a high performance, private, scalable, fast and efficient distributed network.
Integrity Envelopes enhance digital trust with automated, portable, and instantly verifiable digital assets that easily integrate into your business and accounting systems.
Cryptographic Proof of Provenance
Distributed Asset Ledger
Micropayments
High Performance & Low Carbon
Explore CDO Magazine Articles:
The Smart Data Protocol: Combining Web3 Innovations With Proven Enterprise Data Technologies
By transforming digital assets into digital bearer instruments that remain unique, verifiable, and trusted, the Toda Protocol ensures the integrity of digital assets, making them highly reliable for applications that require transparent and tamper-proof provenance.

The Solid Protocol’s focus on decentralized identity ensures that individuals are not reliant on centralized ‘platforms’ for their identities, giving them the freedom to choose identity providers they trust and seamlessly switch between providers without losing their data.
Solid Protocol
Ownership Envelopes
The Solid Protocol addresses the problems of centralized ‘platform dependent’ identity systems, lack of data control, data silos, and data fragmentation.
Decentralized Identity
Data Ownership
Data Portability
User Driven Personalization
Sematic Data
Explore Solid Community Posts:
Smart Data Protocol Intelligent Envelopes
Programmability
Programmability adds intelligent capabilities to your digital assets that provide self-awareness and intelligence. Here are a few examples:
- Add location and device awareness that controls where others are allowed to interact with your Digital Assets.
- Add remote security scans and forensic evidence collection to independently comply with Breach Notification regulations.
- Add privacy preserving data interactions that ensure compliance use of shared data without revealing the source data.
Create your own Data Apps that add intelligence to your data as it flows across multi-party data transactions.
PETs (Privacy Enhancing Technologies)
Composability
Composability allows data owners to combine and integrate different digital assets to create new applications. It increases productivity by reusing digital assets and promoting data modularity. Complex digital assets can be composed from many simple digital assets from many different data owners. It facilitates the composition of data processing pipelines while ensuring data provenance for each individual digital asset.
Smart Contracts
Intelligent Envelopes support the execution of smart contracts across composite digital assets where different components are bound to different data owners, enabling the automation and enforcement of business rules and agreements across multi-party transactions and composite Digital Assets. Data owners can streamline their operations, eliminate intermediaries, and ensure transparency and integrity of their multi-party digital transactions.
Interoperability
Interoperability enables data owners to exchange and use data seamlessly between different systems, platforms, or applications. It facilitates data sharing, collaboration, and integration between different systems and enhances productivity, efficiency, and the ability to integrate data from diverse sources into diverse destinations. It eliminates data silos and promotes compliant and risk-managed collaboration between teams or organizations.
Explore CDO Magazine Articles:
Privacy Enhanced Technologies (PETs) Enable Unimaginable Data Sharing Opportunities
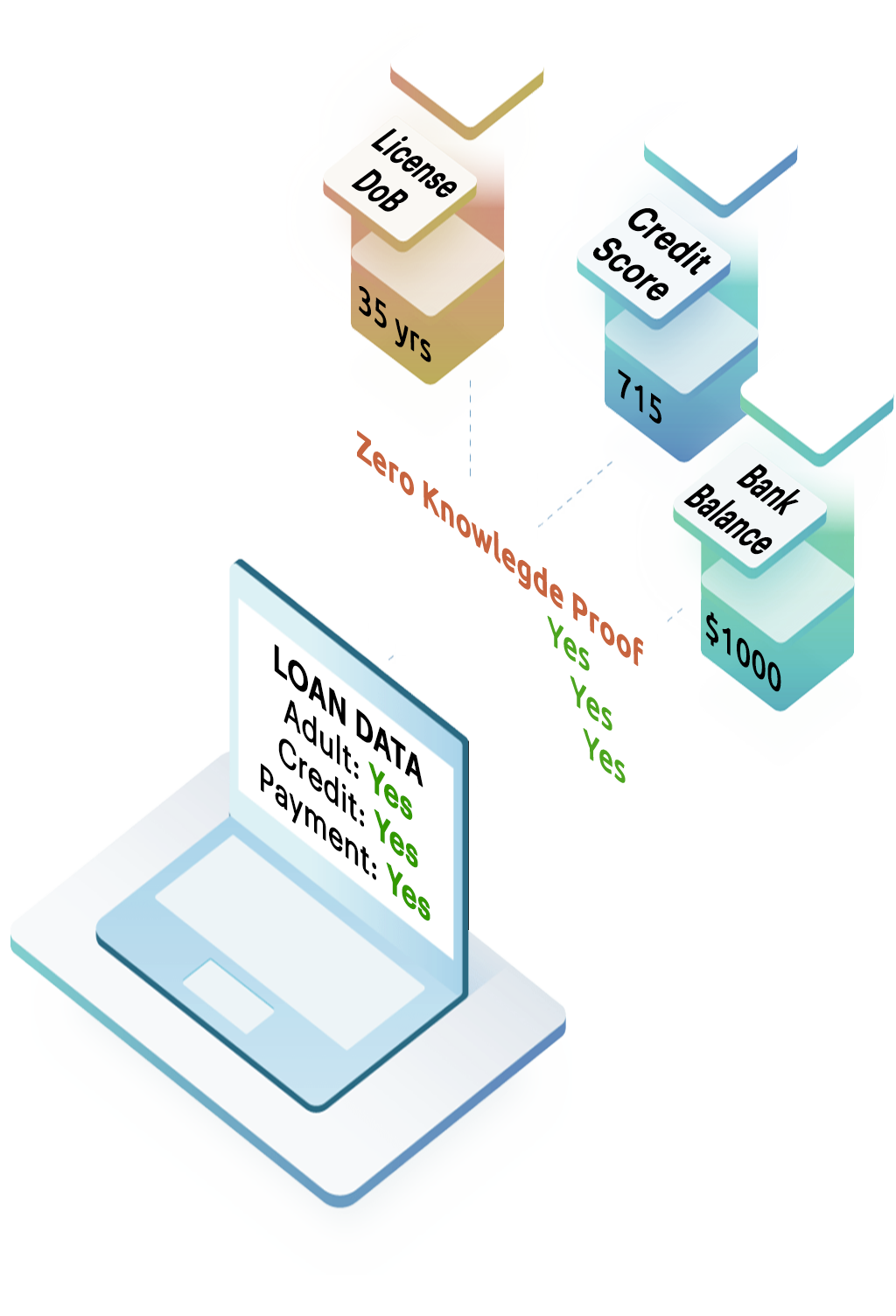
Intelligence Envelopes offer data owners the ability to add new functionality to Digital Assets by packaging Data Apps into Intelligent Envelopes that give the contained data self awareness and environment responsiveness.
