Data Liquidity Protocol Transforms Raw Data
into a Profit Center
Data Products with Proof of Value
The Data Liquidity Protocol unleashes your high-value data use cases by monetizing every Data Product interaction without revealing the secured data inside.
Technical Construction
& Operation
Just as financial liquidity allows assets to be converted into cash, data liquidity enables data to generate value across different systems, organizations, and industries, with minimal friction and maximum security.

It makes every digital file verifiable, secure, compliant, and revenue-ready, so you can control and monetize your data products created from your digital files and data.
DLP binds five cryptographic proofs directly to the file itself:
-
Proof of Integrity – Provenance you can verify.
-
Proof of Ownership – Enforceable rights in your control.
-
Proof of Security – Layered cryptographic protection.
-
Proof of Compliance – Privacy built into the file.
-
Proof of Value – Measurable ROI from every use.
By leveraging the Data Liquidity Protocol, you can trust each data asset as well as the entire system of digital value creation.
This holistic approach secures your data products, digital assets, and files while positioning them as valuable, marketable resources in the digital economy.

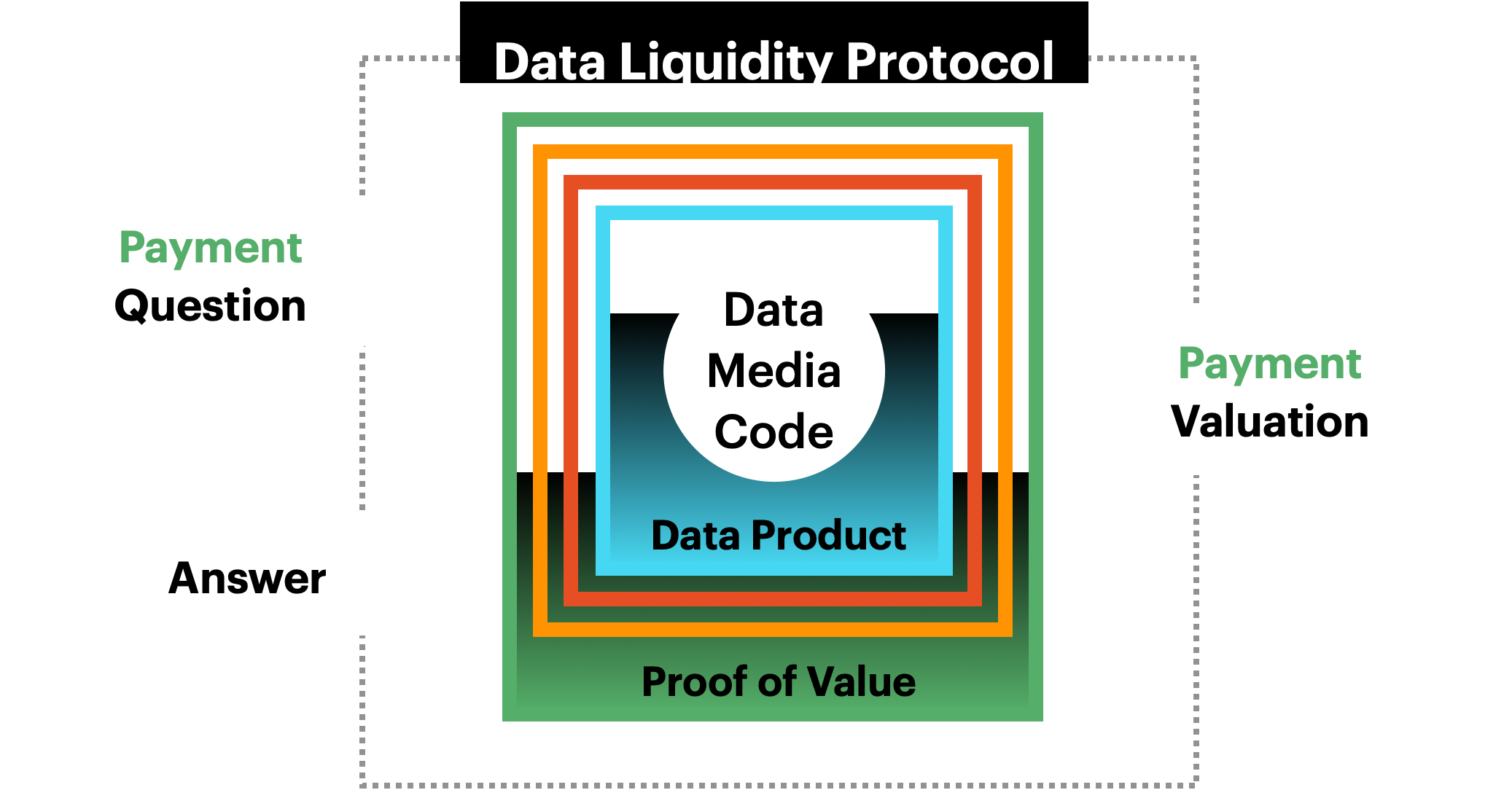
Data Liquidity Benefits:
- Never Reveal Protected Data.
- Price Defined by Value of Answers.
- Payment from Every Interaction.
- Trusted Data Financial Assets.
- Data Leaders as Profit Centers.
Just like a tiny software vending machine, the Digital Rule of Law Patent Pool turns Data, Media, Files, and Code into Financial Assets by securing sensitive data and files inside Data Products that collect payment for every interaction.
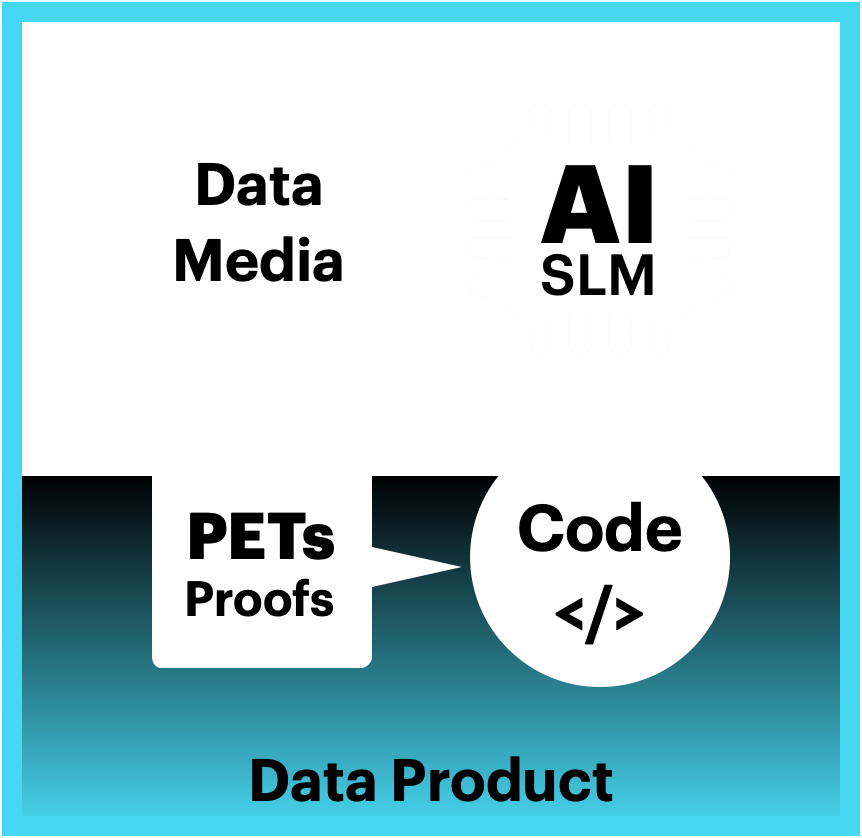
Standardized Data Products
Data Liquidity turns your digital files and data into self-protecting, self-governing Data Products. Each Data Product is wrapped in Security, Integrity, and Intelligent Envelopes that embed:
-
Integrity – Guarantees accuracy and trust.
-
Ownership – Legal title is bound to every file.
- Security – Access is restricted and monitored.
-
Enforcement – Data Contracts are executed automatically.
-
Value – Trustable Data Product ROI.
This design makes data portable, auditable, and monetizable between parties, enforce its own rules, and prove its own value in real time.
Data Products
Data products encapsulate the data itself, metadata about the data, and the logic required to process and interpret the data, promoting the productization and reuse of data products.
Harvard Business Review, “A Better Way to Put Your Data to Work,” maintains that when companies treat their data like a product, they can:
- Reduce the time to implement new data use cases by as much as 90%.
- Decrease their total cost of ownership (technology, development, and maintenance) by up to 30%.
Privacy Enhanced Technologies (PETs & Proofs)
Privacy Enhanced Technologies (PETs) allow data to be monetized safely while retaining complete control and security. The Data Liquidity Protocol embeds two critical capabilities directly inside every Data Product:
-
Privacy-Enhancing Technologies (PETs) – Control how data is used without relying on external systems or revealing the contained data. PETs and Proofs execute inside the data product itself, enabling multiparty collaboration and monetization without exposure.
-
Cryptographic Proofs – Provide evidence of ownership, integrity, security, compliance, and value. Data Liquidity Protocol transforms proofs into revenue events. Each proof can be priced based on the value of the action, the insight, or even the question asked of your data, without revealing or transferring the contained data.
Unlike traditional approaches, our patented design binds PETs to the data product file itself, ensuring privacy, security and integrity are portable, enforceable, and permanent wherever your data flows and grows.
AI Small Langauge Models (AI SLM)
The Data Liquidity Protocol can combine and package Small Language Model (SLM) with other knowledge sources and code libraries into discreet value creating AI Products. The AI model inherits the same ownership, enforcement, audit, and monetization controls as the data it processes.
This lets AI “go to the data” instead of “moving data to the AI”, enabling governed, portable, revenue-generating intelligent AI compute, metered like a digital vending machine.
Integrity Envelopes
Integrity Envelopes are foundational to the Data Liquidity Protocol, designed to ensure the authenticity, reliability, and trustworthiness of your data products.
By leveraging advanced cryptographic primitives called Fair Exchange Protocols, Integrity Envelopes provide a robust framework for maintaining the integrity of data throughout its lifecycle.
Proof of Integrity
Proof of Integrity is a foundational aspect of Integrity Envelopes, ensuring that data remains accurate, reliable, and unaltered. This is achieved through a file-based (off chain) cryptographic proof of provenance, which tracks and verifies the origin and history of each data product.
Key Features:
- Cryptographic Proof of Provenance: Utilizes digital signatures and immutable file-based audit logs to provide a verifiable record of the data product’s origin and history.
- Data Accuracy and Reliability: Ensures that the internal audit log is protected against manipulation and unauthorized changes, maintaining its integrity and trustworthiness.
Proof of Ownership
Proof of Ownership within Integrity Envelopes ensures that data ownership and title are clearly defined, verifiable, and enforceable. This capability is crucial for establishing trust and enabling the monetization of data products.
Ownership Rights: Clearly asserts and verifies ownership rights, ensuring that data owners retain control and authority over their data products.
Digital Cash Micropayments
The TODAQ Micropayment System build upon the Integrity Envelope technology enables cash-like peer-to-peer (P2P) Off-Chain private micropayments. It supports secure payments between parties without the need for payment intermediaries and provides real-time, one-tap micropayments for any digital content and services without login, wallets, or subscriptions.
- Secure Payments: Facilitates secure, private micropayments between parties, reducing the need for payment intermediaries.
- Real-Time Transactions: Enables instant payments, accelerating cash cycles and reducing processing costs.
- Low Carbon Footprint: Designed for sustainability, ensuring low payment processing fees and fast transaction confirmation times.

By transforming digital assets into digital bearer instruments that remain unique, verifiable, and trusted, the Integrity Envelope ensures the provenance of your data products.
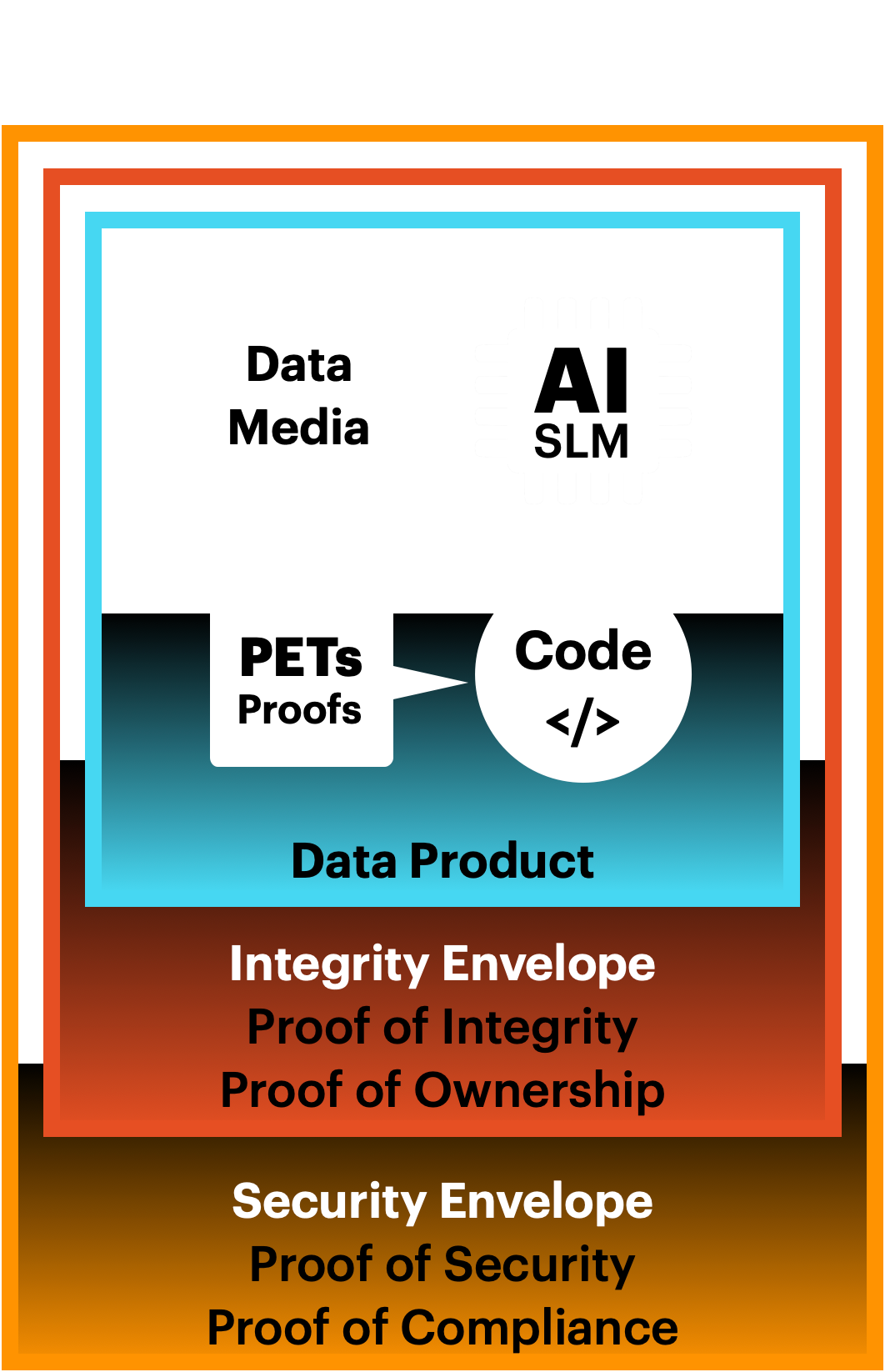
Security Envelopes
Proof of Security
Proof of Security within Security Envelopes ensures that your data is protected through a multi-layered security approach.
Key Features:
- Data Masking and Obfuscation: Employs data masking and obfuscation to ensure that sensitive information is protected and only accessible to authorized parties.
- Data Contracts: Implements granular access control mechanisms to regulate who, where, when and how others can access and modify data, ensuring that only authorized users and systems can interact with your data products.
Proof of Compliance
Proof of Compliance within Security Envelopes ensures that your data usage adheres to global privacy and data protection regulations. This is achieved through the binding of data contracts and privacy preserving proofs to individual data products, that enforce compliant and ethical data processing.
Key Features:
- Data Contracts: Enables the automation and enforcement of business rules and agreements across multiparty transactions, ensuring that data usage complies with legal and regulatory standards.
- Regulatory Adherence: Ensures that data handling practices comply with global privacy and data protection regulations, reducing the risk of non-compliance and associated penalties.
Intelligent Envelopes
Intelligent Envelopes are designed to enhance the functionality and value of data products through dynamic binding of programs and proofs with dynamic functionality, environment awareness, and intelligent responses to evolving threats.
Proof of Value
Proof of Value is the culmination of the capabilities provided by Intelligent Envelopes, ensuring that data products are not only secure and compliant but also prove their value and marketability.
This is achieved through the integration of proofs of integrity, ownership, security, and compliance, which collectively proves the economic potential of each data product.
Key Features:
- Integrated Proofs: Combines proofs of integrity, ownership, security, and compliance to create a comprehensive framework for verifying and enhancing the value of data products.
- Marketability: Positions data products as trusted, valuable resources in the digital economy, opening up new revenue streams and economic opportunities.
- Economic Potential: Enhances the return on investment (ROI) of data products by ensuring their accuracy, reliability, and compliance, dramatically increasing the value of data products.
Data Product Standardization
Data Product Standardization ensures that data products are fluid, interoperable, and easily tradable.
Key Features:
- Programmability: Intelligent Envelopes dynamically bind proofs and programs to data products and ensuring they can be enhanced as new needs arise.
- Composability: Complex data products can be composed from many simple data products from many different data owners. Composability increases liquidity by reusing and nesting data products while promoting data and software modularity.
- Interoperability: Ensures that data products can be easily integrated and utilized across diverse systems and organizations, promoting collaboration and innovation
Standardization ensures data interoperability and security across different systems and organizations, promoting transparency and collaboration while avoiding vendor lock-in.
The Data Liquidity Protocol standard changes the entire digital economy by fundamentally upgrading the structure of data into an intelligent, environment responsive, self-protecting discrete unit of verifiable value.

Intelligence Envelopes offer data owners the ability to add new functionality to Digital Assets by packaging programs and proofs into Intelligent Envelopes that give the contained data self awareness and environment responsiveness.
Standardized Data Products

Data Liquidity turns your digital files and data into self-protecting, self-governing Data Products. Each Data Product is wrapped in Security, Integrity, and Intelligent Envelopes that embed:
-
Integrity – Guarantees accuracy and trust.
-
Ownership – Legal title is bound to every file.
- Security – Access is restricted and monitored.
-
Enforcement – Data Contracts are executed automatically.
-
Value – Trustable Data Product ROI.
This design makes data portable, auditable, and monetizable between parties, enforce its own rules, and prove its own value in real time.
Data Products
Data products encapsulate the data itself, metadata about the data, and the logic required to process and interpret the data, promoting the productization and reuse of digital assets.
Harvard Business Review, “A Better Way to Put Your Data to Work,” maintains that when companies treat their data like a product, they can:
- Reduce the time to implement new data use cases by as much as 90%.
- Decrease their total cost of ownership (technology, development, and maintenance) by up to 30%.
Privacy Enhanced Technologies (PETs & Proofs)
Privacy Enhanced Technologies (PETs) allow data to be monetized safely while retaining complete control and security. The Data Liquidity Protocol embeds two critical capabilities directly inside every Data Product:
-
Privacy-Enhancing Technologies (PETs) – Control how data is used without relying on external systems or revealing the contained data. PETs and Proofs execute inside the data product itself, enabling multiparty collaboration without exposure.
-
Cryptographic Proofs – Provide evidence of ownership, integrity, security, compliance, and value. Data Liquidity Protocol transforms proofs into revenue events. Each proof can be priced based on the value of the action, the insight, or even the question asked of your data, without revealing or transferring the contained data.
Unlike traditional approaches where PETs and proofs exist outside the file, our patented design binds them to the data product file itself, ensuring privacy, security and integrity are portable, enforceable, and permanent wherever your data flows and grows.
AI Small Langauge Models (AI SLM)
The Data Liquidity Protocol can combine and package Small Language Model (SLM) with other knowledge sources and code libraries into discreet value creating AI Products. The AI model inherits the same ownership, enforcement, audit, and monetization controls as the data it processes.
This lets AI “go to the data” instead of “moving data to the AI”, enabling governed, portable, revenue-generating intelligent AI compute, metered like a digital vending machine.
Integrity Envelopes

Integrity Envelopes are foundational to the Data Liquidity Protocol, designed to ensure the authenticity, reliability, and trustworthiness of your data products.
By leveraging advanced cryptographic primitives called Fair Exchange Protocols, Integrity Envelopes provide a robust framework for maintaining the integrity of data throughout its lifecycle.
Proof of Integrity
Proof of Integrity is a foundational aspect of Integrity Envelopes, ensuring that data remains accurate, reliable, and unaltered. This is achieved through a file-based (off chain) cryptographic proof of provenance, which tracks and verifies the origin and history of each data product.
Key Features:
- Cryptographic Proof of Provenance: Utilizes digital signatures and immutable file-based audit logs to provide a verifiable record of the data product’s origin and history.
- Data Accuracy and Reliability: Ensures that the internal audit log is protected against manipulation and unauthorized changes, maintaining its integrity and trustworthiness.
Proof of Ownership
Proof of Ownership within Integrity Envelopes ensures that data ownership and title are clearly defined, verifiable, and enforceable. This capability is crucial for establishing trust and enabling the monetization of data products.
Ownership Rights: Clearly asserts and verifies ownership rights, ensuring that data owners retain control and authority over their data products.
Digital Cash Micropayments
The TODAQ Micropayment System build upon the Integrity Envelope technology enables cash-like peer-to-peer (P2P) Off-Chain private micropayments. It supports secure payments between parties without the need for payment intermediaries and provides real-time, one-tap micropayments for any digital content and services without login, wallets, or subscriptions.
- Secure Payments: Facilitates secure, private micropayments between parties, reducing the need for payment intermediaries.
- Real-Time Transactions: Enables instant payments, accelerating cash cycles and reducing processing costs.
- Low Carbon Footprint: Designed for sustainability, ensuring low payment processing fees and fast transaction confirmation times.
By transforming digital assets into digital bearer instruments that remain unique, verifiable, and trusted, the Integrity Envelope ensures the provenance of your data products.
Security Envelopes

Proof of Security
Proof of Security within Security Envelopes ensures that your data is protected through a multi-layered security approach.
Key Features:
- Data Masking and Obfuscation: Employs data masking and obfuscation to ensure that sensitive information is protected and only accessible to authorized parties.
- Access Control: Implements granular access control mechanisms to regulate who, where, when and how others can access and modify data, ensuring that only authorized users and systems can interact with your data products.
Proof of Compliance
Proof of Compliance within Security Envelopes ensures that your data usage adheres to global privacy and data protection regulations. This is achieved through the binding of data contracts and privacy preserving proofs to individual data products, that enforce compliant and ethical data processing.
Key Features:
- Data Contracts: Enables the automation and enforcement of business rules and agreements across multiparty transactions, ensuring that data usage complies with legal and regulatory standards.
- Regulatory Adherence: Ensures that data handling practices comply with global privacy and data protection regulations, reducing the risk of non-compliance and associated penalties.
Intelligent Envelopes

Intelligent Envelopes are designed to enhance the functionality and value of data products through dynamic binding of programs and proofs with dynamic functionality, environment awareness, and intelligent responses to evolving threats.
Proof of Value
Proof of Value is the culmination of the capabilities provided by Intelligent Envelopes, ensuring that data products are not only secure and compliant but also prove their value and marketability.
This is achieved through the integration of proofs of integrity, ownership, security, and compliance, which collectively proves the economic potential of each data product.
Key Features:
- Integrated Proofs: Combines proofs of integrity, ownership, security, and compliance to create a comprehensive framework for verifying and enhancing the value of data products.
- Marketability: Positions data products as trusted, valuable resources in the digital economy, opening up new revenue streams and economic opportunities.
- Economic Potential: Enhances the return on investment (ROI) of data assets by ensuring their accuracy, reliability, and compliance, dramatically increasing the value of data products.
Data Product Standardization
Data Product Standardization ensures that data products are fluid, interoperable, and easily tradable.
Key Features:
- Programmability: Intelligent Envelopes dynamically bind proofs and programs to data products and ensuring they can be enhanced as new needs arise.
- Composability: Complex data products can be composed from many simple data products from many different data owners. Composability increases liquidity by reusing and nesting data products while promoting data and software modularity.
- Interoperability: Ensures that data products can be easily integrated and utilized across diverse systems and organizations, promoting collaboration and innovation
Standardization ensures data interoperability and security across different systems and organizations, promoting transparency and collaboration while avoiding vendor lock-in.
The Data Liquidity Protocol standard changes the entire digital economy by fundamentally upgrading the structure of data into an intelligent, environment responsive, self-protecting discrete unit of verifiable value.
Intelligence Envelopes offer data owners the ability to add new functionality to Digital Assets by packaging programs and proofs into Intelligent Envelopes that give the contained data self awareness and environment responsiveness.
